Countryside VoIP Setup 2.6 2016-09-10
Changelog 2.5 -> 2.6:
Channel changed to make Sony's cell phone Xperia ST21i with Android 4.0.4 connecting.
Router: Wireless: Basic Settings: ath0: ath0: Wireless Channel: 13 - 2472 MHz -> 9 - 2452 MHz
Some clean up
Bridge: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): Use DNSMasq for DHCP: yes -> no
Bridge: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): Use DNSMasq for DNS: yes -> no
Bridge: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): DHCP-Authoritative: yes -> no
Same channel is used now to make the things easier for certain stupid devices
Bridge: Wireless: Basic Settings: wl0: wl0: Wireless Channel: 1 - 2412 MHz -> 9 - 2452 MHz
Modem box hardware design philosophy:
The modem box is a point where at least two different networks join, the electrical power network and
the telephone network. In the countryside both may come through overhead lines, representing the worst
case. In the present case, the central office is connected via an underground cable, but the electricity
comes through an overhead power line. So the modem box does contain some surge protection devices keeping
both the networks down as the final part of a lightning protection system.
On the other hand, the equipment of that box is kept cheap using off-the-shelf components
and the computer network is galvanically separated from that point by means of 30 m optical fiber.
The rock solid enclosure prevents dust and spiders from entering and fire from leaving.
Special wiring ensures that a buzzer sounds when the surge arrester signals
that the varistor has to be replaced. That buzzer can manually be switched off.
The total power consumption of the modem box is 13 W and the power failure bridging time is half an hour.
Note that, because both the modem and the media converter are powered by the same AC adapter where the
negative DC output is grounded, the connection between these units is done using an UTP cable.
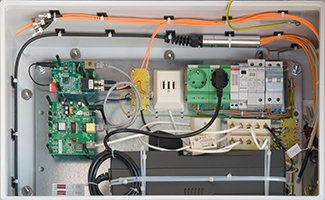 |
Photograph 1: Modem box
Modem box hardware:
Enclosure: Rittal Standard Enclosure 1101.030, 400x650x250mm³, IP69K
DIN Rail Circuit breaker: Hager MCN206, 2 pole, 6kA C-6A 2M
DIN Rail Surge Protection Device: Finder 7P.22.8.275.1020, Type 2 Surge Arrester
DIN Rail On-Off Switch: Doepke On-Off Switch, single pole, 16A RSS 016-100
DIN Rail Buzzer: ABB 2CSM232000R0821 RM2-230 230VAC, 50Hz
DIN Rail Power Outlets: Phoenix Contact SD-D/SC
UPS: APC BE325-GR SurgeArrest + Battery Backup 325VA
AC Adapter: Dehner Elektronik SYS 1449-1505-W2E, 5VDC 3A
PPA: Diode + Resistor 470kΩ 1%
6P4C Patch Fields: Noname
DSL Filter: Excelsus Z-Blocker Model Z-230PJ, 0.2B
ADSL Modem: D-Link DSL-321B, Annex B, Hardware version D2, Firmware version DE_1.03, 5VDC
Heatsink: Fischer Elektronik ICK S 14X14X10 9.8K/W
Media Converter: EL022V2, 10/100TX-100FX, ST, Multimode, 1310nm, LFP function, 5VDC
Cable Spider Fan Out Kit: JES Fan Out Kit 6-way, similar to FOP KAT-12-06-BS
Optical Fiber: U-DQ(ZN) BH 08G 50/125μ OM3
Router box hardware design philosophy:
Both the modem box and the router box have to provide reliable Internet service for VoIP phones,
servers and smart devices. The router box has further to provide some reliable backup service.
So, it first of all contains some surge protection devices, too, keeping the electrical power network
down as the final part of a lightning protection system.
The equipment of the router box is potent and optimized for low power consumption.
The rock solid enclosure prevents dust and spiders from entering and fire from leaving.
Special wiring ensures that a buzzer sounds when either the surge arrester signals that the varistor
has to be replaced or the UPS control unit signals that the battery has to be replaced.
That buzzer can manually be switched off.
The two 5 W fans are normally off, but, if the temperature near the top of the box inside is going
to exceed 40°C, then they are switched on to whirl the air around such that the whole box surface
acts as a cooler. The temperature controller switches the fans off again with 4°C hysteresis.
Switching on the fans is more thought of as being an emergency reaction, not a standard one,
because the battery below suffers more if it breathes warm air from the electronic equipment.
In summer, the fans run occasionally if the environment temperature is 30°C or higher.
The total power consumption of the router box is 28 W, whereat that value contains both the power
for one Grandstream GXP2010 telephone, fed via PoE, and the power of 2.5 W for a PowerLAN adapter.
The power failure bridging time is several hours, but, pay attention, on power failures,
the PowerLAN adapter goes down. At the moment, it seems that there is no PowerLAN adapter in the
market that can be supplied with 24 VDC such that DC UPS support can easily be given.
The PowerLAN adapter has been added to study the behavior of that technology in environments
with electrical installations based on rigid wires, as it is the case, for example, in Germany.
As above, internal network cabling is performed in UTP if the involved units are not explicitly
declared as Industrial Ethernet components. Copper network cables passing the box boundaries are Cat6 STP,
however, to prevent ground loops, their shields are cut somewhere in the cable channel through
Cat6 RJ45 UTP inline couplers. It is believed that this is enough in the present case. Another flavor,
completely isolating, would, for example, be to install the Baaske ProTek5 or even the Baaske MI1005
inline network isolators that serve up to 1000BASE-T and 5kVAC.
It should finally be noted here that, for inspecting the router box details,
the below photograph in the middle should be preferred because it is of best quality.
Photographs 2, 3, and 4: Initial router box, current router box, PowerLAN adapter with spacer
Router box hardware:
Enclosure: Rittal Standard Enclosure 1101.030, 400x650x250mm³, IP69K
DIN Rail Circuit breaker: Merlin Gerin Multi9 K60N C6, 2 pole
DIN Rail Surge Protection Device: Finder 7P.22.8.275.1020, Type 2 Surge Arrester
DIN Rail On-Off Switch: Doepke On-Off Switch, single pole, 16A RSS 016-100
DIN Rail Buzzer: ABB 2CSM232000R0821 RM2-230 230VAC, 50Hz
DIN Rail Power Outlet: Phoenix Contact SD-D/SC/YE
DIN Rail Temperature Controller: Ziehl TR111V Temperature Relay for Pt100 Sensors
Pt100 Sensor: Heraeus W-SZK(O) 31.600.393 Sensor, -20...+110°C, Class B
Fans: EBM-Papst 4314, 119x119x32mm³, 2800 RPM, 24VDC, 5W
DIN Rail Power Supply: Puls QS5.241, Output 24V 5A
DIN Rail UPS: Puls DC-UPS Control Unit UB10.241, 24V, 10A
DIN Rail Battery: Puls UZK12.071 Battery Module, 12V, 7Ah
DIN Rail Relay: Weidmüller RIDERSERIES RCIKITP 24VDC 1CO LD, 24VDC
Optical Fiber: U-DQ(ZN) BH 08G 50/125μ OM3
Cable Spider Fan Out Kit: JES Fan Out Kit 6-way, similar to FOP KAT-12-06-BS
Media Converter: EL022V2, 10/100TX-100FX, ST, Multimode, 1310nm, LFP function, 5VDC
DC/DC Converter: XP POWER JTK1524S05, Input 9V to 36V, Output 5V 3A
Router: Gateworks Cambria GW2358-4 Network Platform, Firmware version DD-WRT v24-sp2 (12/14/11) std - build 18007
WLAN Card: Ubiquiti XR2, 32-bit mini-PCI Type IIIA, IEEE 802.11b/g, 2.4GHz, Chipset Atheros, 6th Gen., AR5414
Pigtails: shop.adaptare.de 60331 Pigtail, MMCX male, RP-TNC female, 20cm
Antenna Cables: Linksys AC9TNC, R-TNC female, R-TNC male, 9m, -5dB at 2.4GHz
Antenna: Linksys HGA7T, R-TNC male, 2.4GHz, 7dBi, VSWR < 1.92 (not part of the router box)
Heatsink: Fischer Elektronik ICK S 25X25X18.5 5.2K/W
USB Flash Drive: Transcend TS32GJF600, Read 32MB/s, Write 16MB/s, Operating 0...70°C, 10,000 Erase Cycles
DIN Rail Switch: WAGO Industrial Eco Switch 852-112, 8 ports 10/100Base-TX, 18-30VDC
DIN Rail PoE-I: www.ubf.de 114414007 PoE Injector, 100BaseT, In 9-36V, Out IEEE 802.3af, -40...+85°C
PowerLAN Adapter: AVM FRITZ!Powerline 520E, Firmware 5.2.3-02
PowerLAN Adapter Spacer 1: Brennenstuhl Travel Adapter, Schuko plug -> BS1363 socket, No. 1508530
PowerLAN Adapter Spacer 2: Brennenstuhl Travel Adapter, BS1363 plug -> Schuko socket, No. 1508533
Further hardware of relevance here:
Telephone: Grandstream GXP2010, Hardware version 0.2B, Firmware version 1.2.5.3, Bootloader version 1.1.6.9
Radio: Terratec Noxon Internet Radio For Ipod, Firmware version 3.8.36.6923 (2009-08-26)
UPS: MGE Pulsar 1000 RT2U with Eaton NMC 66102, Card technical level 15, Firmware version HE
Bridge: Linksys WRT54GL v1.1, Firmware version DD-WRT v24-sp2 (08/07/10) mini - build 14896
PowerLAN Adapter: AVM FRITZ!Powerline 520E, Firmware 5.2.3-02
Phase Coupler: Eichhoff KC002-923/203-500, 3x22nF X2, AC 440V, 50/60Hz
Photograph 5: Bridge for WLAN roaming with PowerLAN adapter and wattmeter on an extension cord
Notes on firmware releases:
In general it is a good idea to run the most recent firmware on a particular device.
So one has a never ending pursuit of installing latest firmware releases in front that finally
finishes just in the moment when a device changes its state to become an end-of-live product.
The Grandstream GXP2010 is such a product and the Linksys WRT54GL v1.1 seems to be one.
The things are completely different in the case of the Gateworks Cambria GW2358-4 router board.
With respect to that board the firmware release is critical if it is planned to install third-party
packages as the ones from www.openwrt.org.
Build 18007 is the latest release that still runs Linux 2.6. All the following ones work with
kernels 3.2 and let selected binaries from www.openwrt.org fail with segmentation fault or other
fatal errors. Obviously, the OpenWrt binaries still expect Linux 2.6.
On the other hand, there was a critical bug with respect to the system time management in
builds somewhat smaller than 18007 such that we have to live here with build 18007, exactly,
up to the moment www.openwrt.org also changes to Linux 3.2.
Configuration + Some Info:
Provider Web Page: Annex M: Not enabled, not available
Provider Web Page: Annex L: Not enabled, not available
Provider Web Page: Fastpath: Not enabled, not available
Provider Web Page: DNS Hijacking: Disabled, available
ADSL Modem: Mode: Bridge mode with 1483 bridged IP LLC as the connection type
ADSL Modem: ATM Parameter: Virtual Path Identifier (VPI): 1 (provider-dependent)
ADSL Modem: ATM Parameter: Virtual Channel Identifier (VCI): 32 (provider-dependent)
ADSL Modem: ADSL Modem LAN IP address: Fixed address 192.168.1.1
ADSL Modem: ADSL Modem LAN Subnet Mask: 255.255.255.0
ADSL Modem: Advanced ADSL Settings: Modulation Type: Autosense
ADSL Modem: Advanced ADSL Settings: Capability Bitswap Enable: Yes
ADSL Modem: Advanced ADSL Settings: Capability SRA Enable: No
ADSL Modem: Status Info: Downstream rate: 16272 Kbps (marginally varying)
ADSL Modem: Status Info: Upstream rate: 1179 Kbps (marginally varying)
ADSL Modem: Status Info: Downstream SNR: 6.1 dB (marginally varying)
ADSL Modem: Status Info: Downstream Attenuation: 22.0 dB (marginally varying)
ADSL Modem: Status Info: Upstream SNR: 10.9 dB (marginally varying)
ADSL Modem: Status Info: Upstream Attenuation: 11.5 dB (marginally varying)
Router: Setup: Basic Setup: WAN Setup: WAN connection type: Connection Type: PPPoE
Router: Setup: Basic Setup: WAN Setup: WAN connection type: User Name: <providerUserName>
Router: Setup: Basic Setup: WAN Setup: WAN connection type: Password: <providerPassWord>
Router: Setup: Basic Setup: WAN Setup: Optional Settings: Router Name: scomm
Router: Setup: Basic Setup: WAN Setup: Optional Settings: MTU: Manual 1492
Router: Setup: Basic Setup: WAN Setup: Optional Settings: STP: Disable
Router: Setup: Basic Setup: Network Setup: Router IP: Local IP Address: 10.xxx.yyy.15
Router: Setup: Basic Setup: Network Setup: Router IP: Subnet Mask: 255.255.255.0
Router: Setup: Basic Setup: Network Setup: Router IP: Gateway: 10.xxx.yyy.15
Router: Setup: Basic Setup: Network Setup: Router IP: Local DNS: 10.xxx.yyy.15
Router: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): DHCP Type: DHCP Server
Router: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): DHCP Server: Enable
Router: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): Start IP Address: 10.xxx.yyy.210
Router: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): Static DNS 1: 8.8.8.8
Router: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): Static DNS 2: 8.8.4.4
Router: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): Static DNS 3: 0.0.0.0
Router: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): WINS: 0.0.0.0
Router: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): Use DNSMasq for DHCP: yes
Router: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): Use DNSMasq for DNS: yes
Router: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): DHCP-Authoritative: yes
Router: Setup: Basic Setup: Network Setup: Time Settings: NTP Client: Enable
Router: Setup: Basic Setup: Network Setup: Time Settings: Time Zone: UTP+01:00
Router: Setup: Basic Setup: Network Setup: Time Settings: Summer Time (DST): last Sun Mar - last Sun Oct
Router: Setup: Basic Setup: Network Setup: Time Settings: Server IP/Name: 0.debian.pool.ntp.org
# Begin DDNS
# For DynDNS
#Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: DDNS Service: DynDNS.org
#Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: User Name: <dyndnsUserName>
#Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: Password: <dyndnsPassWord>
#Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: Host Name: <dyndnsHostName>.dyndns.org
#Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: Type: Dynamic
#Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: Wildcard: <empty>
#Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: Do not use external ip check: yes
#Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: Options: Force Update Interval: 10 days
# For Strato
Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: DDNS Service: Custom
Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: DDNS Server: dyndns.strato.com
Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: User Name: <mySecondLevelDomain>.<myTopLevelDomain>
Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: Password: <dyndnsStratoPassWord>
Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: Host Name: <myHostName>.<mySecondLevelDomain>.<myTopLevelDomain>
Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: URL: https://dyndns.strato.com/nic/update?hostname=
Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: Additional DDNS Options: <empty>
Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: Do not use external ip check: yes
Router: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: Options: Force Update Interval: 10 days
# End DDNS
Router: Setup: Advanced Routing: Advanced Routing: Operating Mode: Operating Mode: Gateway
Router: Setup: Networking: Port Setup: Port Setup: WAN Port Assignment: ixp1
Router: Wireless: Basic Settings: ath0: ath0: Wireless Mode: AP
Router: Wireless: Basic Settings: ath0: ath0: Wireless Network Mode: G-Only
Router: Wireless: Basic Settings: ath0: ath0: Channel Width: Full (20 MHz)
Router: Wireless: Basic Settings: ath0: ath0: Wireless Channel: 9 - 2452 MHz
Router: Wireless: Basic Settings: ath0: ath0: Wireless Network Name (SSID): <wlanSsid>
Router: Wireless: Basic Settings: ath0: ath0: Wireless SSID Broadcast: Enable
Router: Wireless: Basic Settings: ath0: ath0: Advanced Settings: yes
Router: Wireless: Basic Settings: ath0: ath0: TX Power: 18 dBm
Router: Wireless: Basic Settings: ath0: ath0: Antenna Gain: 2 dBi
Router: Wireless: Basic Settings: ath0: ath0: Max Associated Clients: 128
Router: Wireless: Basic Settings: Advanced Options: Rate Control Algorithm: Rate Control Algorithm: Minstrel EWMA
Router: Wireless: Wireless Security: ath0: ath0: Security Mode: WPA2 Personal
Router: Wireless: Wireless Security: ath0: ath0: WPA Algorithms: AES
Router: Wireless: Wireless Security: ath0: ath0: WPA Shared Key: <wlanPassWord>
Router: Services: Services: Services Management: DHCP Server: Used Domain: LAN & WLAN
Router: Services: Services: Services Management: DHCP Server: LAN Domain: snet
Router: Services: Services: Services Management: DHCP Server: Static Leases: defined by script SetStaticLeases
Router: Services: Services: Services Management: DNSMasq: DNSMasq: Enable
Router: Services: Services: Services Management: DNSMasq: Local DNS: Disable
Router: Services: Services: Services Management: DNSMasq: No DNS Rebind: Enable
Router: Services: Services: Services Management: Secure Shell: SSHd: Enable
Router: Services: Services: Services Management: Secure Shell: SSH TCP Forwarding: Disable
Router: Services: Services: Services Management: Secure Shell: Password Login: Enable
Router: Services: Services: Services Management: Secure Shell: Port: 22
Router: Services: Services: Services Management: Secure Shell: Authorized Keys: defined by script SetSshdAuthorizedKeys
Router: Services: USB: USB Support: USB Support: Core USB Support: Enable
Router: Services: USB: USB Support: USB Support: USB Storage Support: Enable
Router: Services: Milkfish SIP Router: Milkfish SIP Router: Milkfish SIP Router: SIP Router: Disable
Router: Security: Firewall: Security: Firewall Protection: SPI Firewall: Enable
Router: Security: Firewall: Security: Block WAN Requests: Block Anonymous WAN Requests (ping): Enable
Router: Security: Firewall: Security: Block WAN Requests: Filter Multicast: Enable
Router: Security: Firewall: Security: Block WAN Requests: Filter WAN NAT Redirection: Disable
Router: Security: Firewall: Security: Block WAN Requests: Filter IDENT (Port 113): Enable
Router: Security: Firewall: Security: Block WAN Requests: Block WAN SNMP access: Enable
Router: Security: Firewall: Security: Impede WAN DoS/Bruteforce: Limit SSH Access: Enable
Router: Security: VPN Passthrough: Virtual Private Network (VPN): VPN Passthrough: IPSec Passthrough: Enable
Router: Security: VPN Passthrough: Virtual Private Network (VPN): VPN Passthrough: PPPT Passthrough: Enable
Router: Security: VPN Passthrough: Virtual Private Network (VPN): VPN Passthrough: L2TP Passthrough: Enable
Router: NAT/QoS: Port Forwarding: Port Forward: Forwards: defined by script SetForwardSpec
Router: NAT/QoS: UPnP: Universal Plug and Play (UPnP): UPnP Configuration: UPnP Service: Disable
Router: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Start QoS: Enable
Router: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Port: WAN
Router: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Packet Scheduler: HTB
Router: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Uplink (kbps): 1000
Router: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Downlink (kbps): 15000
Router: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Optimize for Gaming: yes
Router: NAT/QoS: QoS: Quality of Service (QoS): Services Priority: ntp: Premium
Router: NAT/QoS: QoS: Quality of Service (QoS): Services Priority: rtp: Premium
Router: NAT/QoS: QoS: Quality of Service (QoS): Services Priority: sip: Express
Router: NAT/QoS: QoS: Quality of Service (QoS): MAC Priority: Grandstream GXP2010 Phone: WAN Max Up 200 kbps
Router: NAT/QoS: QoS: Quality of Service (QoS): MAC Priority: Grandstream GXP2010 Phone: WAN Max Down 200 kbps
Router: NAT/QoS: QoS: Quality of Service (QoS): MAC Priority: Grandstream GXP2010 Phone: LAN Max 200 kbps
Router: NAT/QoS: QoS: Quality of Service (QoS): MAC Priority: Terratec Noxon Internet Radio: WAN Max Up 200 kbps
Router: NAT/QoS: QoS: Quality of Service (QoS): MAC Priority: Terratec Noxon Internet Radio: WAN Max Down 200 kbps
Router: NAT/QoS: QoS: Quality of Service (QoS): MAC Priority: Terratec Noxon Internet Radio: LAN Max 200 kbps
Router: NAT/QoS: QoS: Quality of Service (QoS): Default Bandwidth Level: Enable Per User Default Limits: Disable
Router: NAT/QoS: QoS: Quality of Service (QoS): Default Bandwidth Level: WAN Bandwidth in kbps Up: 800
Router: NAT/QoS: QoS: Quality of Service (QoS): Default Bandwidth Level: WAN Bandwidth in kbps Down: 12000
Router: NAT/QoS: QoS: Quality of Service (QoS): Default Bandwidth Level: LAN Bandwidth in kbps: 50000
Router: Administration: Management: Router Management: Router Password: Router Username: root
Router: Administration: Management: Router Management: Router Password: Router Password: <routerPassWord>
Router: Administration: Management: Router Management: Web Access: Protocol: HTTP: Enable
Router: Administration: Management: Router Management: Web Access: Protocol: HTTPS: Enable
Router: Administration: Management: Router Management: Web Access: Enable Info Site: Disable
Router: Administration: Management: Router Management: Remote Access: Web GUI Management: Enable
Router: Administration: Management: Router Management: Remote Access: Use HTTPS: Enable
Router: Administration: Management: Router Management: Remote Access: Web GUI Port: 8443
Router: Administration: Management: Router Management: Remote Access: SSH Management: Enable
Router: Administration: Management: Router Management: Remote Access: SSH Remote Port: 22
Router: Administration: Management: Router Management: Remote Access: Allow Any Remote IP: Enable
Router: Administration: Management: Router Management: Cron: Cron: Enable
Router: Administration: Management: Router Management: Cron: Additional Cron Jobs: Line 1: 17 3 * * * root /jffs/usr/bin/DlinkDsl320bReboot
Router: Administration: Management: Router Management: Cron: Additional Cron Jobs: Line 2: 27 3 * * * root /jffs/usr/bin/GrandstreamGxp2010Reboot
Router: Administration: Management: Router Management: Cron: Additional Cron Jobs: Line 3: 32 3 * * * root /jffs/usr/bin/EatonNmc66102Reboot
Router: Administration: Management: Router Management: Routing: Routing: Disable
Router: Administration: Management: Router Management: IPv6 Support: IPv6: Disable
Router: Administration: Management: Router Management: JFFS2 Support: JFFS2: Enable
Router: Administration: Management: Router Management: JFFS2 Support: Clean JFFS2: Enable (gets disabled by itself)
Router: Administration: Management: Router Management: Overclocking: Not Supported
Router: Administration: Management: Router Management: CIFS Automount: Common Internet File System: Disable
Router: Administration: Keep Alive: Schedule Reboot: Schedule Reboot: Enable
Router: Administration: Keep Alive: Schedule Reboot: At a set Time: Enable 03:22 Everyday
Router: Administration: Commands: Diagnostics: Startup: Line 1: mount -o ro,remount /jffs
Router: Administration: Commands: Diagnostics: Startup: Line 2: /jffs/usr/bin/UpdateLdSoCache
Router: Administration: Commands: Diagnostics: Startup: Line 3: /jffs/usr/bin/UpdateCert
Router: Administration: Commands: Diagnostics: Startup: Line 4: /jffs/usr/bin/MountExternalMemory
Router: Administration: Commands: Diagnostics: Firewall: Line 1: ifconfig ixp1 192.168.1.15 netmask 255.255.255.0
Router: Administration: Commands: Diagnostics: Firewall: Line 2: iptables -t nat -I POSTROUTING -o ipx1 -d 192.168.1.15/24 -j MASQUERADE
Router: Administration: Commands: Diagnostics: Firewall: Line 3: /jffs/usr/bin/FixCronBug
Bridge: Setup: Basic Setup: WAN Setup: WAN connection type: Connection Type: Disabled
Bridge: Setup: Basic Setup: WAN Setup: WAN connection type: STP: Disable
Bridge: Setup: Basic Setup: WAN Setup: Optional Settings: Router Name: wa1
Bridge: Setup: Basic Setup: WAN Setup: Optional Settings: MTU: Manual 1492
Bridge: Setup: Basic Setup: Network Setup: Router IP: Local IP Address: 10.xxx.yyy.151
Bridge: Setup: Basic Setup: Network Setup: Router IP: Subnet Mask: 255.255.255.0
Bridge: Setup: Basic Setup: Network Setup: Router IP: Gateway: 10.xxx.yyy.15
Bridge: Setup: Basic Setup: Network Setup: Router IP: Local DNS: 10.xxx.yyy.15
Bridge: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): DHCP Type: DHCP Server
Bridge: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): DHCP Server: Disable
Bridge: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): Use DNSMasq for DHCP: no
Bridge: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): Use DNSMasq for DNS: no
Bridge: Setup: Basic Setup: Network Setup: Network Address Server Settings (DHCP): DHCP-Authoritative: no
Bridge: Setup: Basic Setup: Network Setup: Time Settings: NTP Client: Enable
Bridge: Setup: Basic Setup: Network Setup: Time Settings: Time Zone: UTP+01:00
Bridge: Setup: Basic Setup: Network Setup: Time Settings: Summer Time (DST): last Sun Mar - last Sun Oct
Bridge: Setup: Basic Setup: Network Setup: Time Settings: Server IP/Name: 0.debian.pool.ntp.org
Bridge: Setup: DDNS: Dynamic Domain Name System (DDNS): DDNS: DDNS Service: Disable
Bridge: Setup: Advanced Routing: Advanced Routing: Operating Mode: Operating Mode: Router
Bridge: Setup: Networking: Port Setup: Port Setup: WAN Port Assignment: vlan1
Bridge: Wireless: Basic Settings: wl0: wl0: Wireless Mode: AP
Bridge: Wireless: Basic Settings: wl0: wl0: Wireless Network Mode: G-Only
Bridge: Wireless: Basic Settings: wl0: wl0: Wireless Network Name (SSID): <wlanSsid>
Bridge: Wireless: Basic Settings: wl0: wl0: Wireless Channel: 9 - 2452 MHz
Bridge: Wireless: Basic Settings: wl0: wl0: Wireless SSID Broadcast: Enable
Bridge: Wireless: Basic Settings: wl0: wl0: Network Configuration: Bridged
Bridge: Wireless: Wireless Security: wl0: wl0: Security Mode: WPA2 Personal
Bridge: Wireless: Wireless Security: wl0: wl0: WPA Algorithms: AES
Bridge: Wireless: Wireless Security: wl0: wl0: WPA Shared Key: <wlanPassWord>
Bridge: Wireless: Advanced Settings: Advanced Wireless Settings: Advanced Settings: Max Associated Clients: 128
Bridge: Wireless: Advanced Settings: Advanced Wireless Settings: Advanced Settings: TX Power: 71 mW
Bridge: Services: Services: Services Management: DNSMasq: DNSMasq: Disable
Bridge: Services: Services: Services Management: Secure Shell: SSHd: Enable
Bridge: Services: Services: Services Management: Secure Shell: SSH TCP Forwarding: Disable
Bridge: Services: Services: Services Management: Secure Shell: Password Login: Enable
Bridge: Services: Services: Services Management: Secure Shell: Port: 22
Bridge: Services: Services: Services Management: Secure Shell: Authorized Keys: defined by script SetSshdAuthorizedKeys
Bridge: Security: Firewall: Security: Firewall Protection: SPI Firewall: Enable
Bridge: Security: Firewall: Security: Block WAN Requests: Block Anonymous WAN Requests (ping): Enable
Bridge: Security: Firewall: Security: Block WAN Requests: Filter Multicast: Enable
Bridge: Security: Firewall: Security: Block WAN Requests: Filter WAN NAT Redirection: Disable
Bridge: Security: Firewall: Security: Block WAN Requests: Filter IDENT (Port 113): Enable
Bridge: Security: VPN Passthrough: Virtual Private Network (VPN): VPN Passthrough: IPSec Passthrough: Enable
Bridge: Security: VPN Passthrough: Virtual Private Network (VPN): VPN Passthrough: PPPT Passthrough: Enable
Bridge: Security: VPN Passthrough: Virtual Private Network (VPN): VPN Passthrough: L2TP Passthrough: Enable
Bridge: NAT/QoS: Port Forwarding: Port Forward: Forwards: none
Bridge: NAT/QoS: UPnP: Universal Plug and Play (UPnP): UPnP Configuration: UPnP Service: Disable
Bridge: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Start QoS: Enable
Bridge: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Port: LAN & WLAN
Bridge: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Packet Scheduler: HTB
Bridge: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Uplink (kbps): 50000
Bridge: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Downlink (kbps): 50000
Bridge: NAT/QoS: QoS: Quality of Service (QoS): QoS Settings: Optimize for Gaming: yes
Bridge: NAT/QoS: QoS: Quality of Service (QoS): Services Priority: ntp: Premium
Bridge: NAT/QoS: QoS: Quality of Service (QoS): Services Priority: rtp: Premium
Bridge: NAT/QoS: QoS: Quality of Service (QoS): Services Priority: sip: Express
Bridge: NAT/QoS: QoS: Quality of Service (QoS): MAC Priority: Grandstream GXP2010 Phone: Premium
Bridge: NAT/QoS: QoS: Quality of Service (QoS): MAC Priority: Terratec Noxon Internet Radio: Express
Bridge: NAT/QoS: QoS: Quality of Service (QoS): Ethernet Port Priority: Port 1: Exempt 100M
Bridge: NAT/QoS: QoS: Quality of Service (QoS): Ethernet Port Priority: Port 2: Exempt 100M
Bridge: NAT/QoS: QoS: Quality of Service (QoS): Ethernet Port Priority: Port 3: Exempt 100M
Bridge: NAT/QoS: QoS: Quality of Service (QoS): Ethernet Port Priority: Port 4: Exempt 100M
Bridge: Administration: Management: Router Management: Router Password: Router Username: root
Bridge: Administration: Management: Router Management: Router Password: Router Password: <routerPassWord>
Bridge: Administration: Management: Router Management: Web Access: Protocol: HTTP: Enable
Bridge: Administration: Management: Router Management: Web Access: Enable Info Site: Disable
Bridge: Administration: Management: Router Management: Remote Access: Web GUI Management: Disable
Bridge: Administration: Management: Router Management: Remote Access: SSH Management: Enable
Bridge: Administration: Management: Router Management: Remote Access: SSH Remote Port: 22
Bridge: Administration: Management: Router Management: Remote Access: Allow Any Remote IP: Enable
Bridge: Administration: Management: Router Management: Cron: Cron: Enable
Bridge: Administration: Management: Router Management: Cron: Additional Cron Jobs: <empty>
Bridge: Administration: Management: Router Management: Routing: Routing: Enable
Bridge: Administration: Management: Router Management: JFFS2 Support: JFFS2: Enable
Bridge: Administration: Management: Router Management: JFFS2 Support: Clean JFFS2: Enable (gets disabled by itself)
Bridge: Administration: Management: Router Management: Overclocking: Frequency: 216 MHz
Bridge: Administration: Keep Alive: Schedule Reboot: Schedule Reboot: Enable
Bridge: Administration: Keep Alive: Schedule Reboot: At a set Time: Enable 03:12 Everyday
Bridge: Administration: Commands: Diagnostics: Startup: mount -o ro,remount /jffs
Bridge: Administration: Commands: Diagnostics: Firewall: <empty>
Phone: Basic Settings: End User Password: <telUserPassWord>
Phone: Basic Settings: Statically configured: Yes
Phone: Basic Settings: IP address: 10.xxx.yyy.71
Phone: Basic Settings: Subnet Mask: 255.255.255.0
Phone: Basic Settings: Gateway: 10.xxx.yyy.15
Phone: Basic Settings: DNS Server 1: 10.xxx.yyy.15
Phone: Basic Settings: DNS Server 2: 0.0.0.0
Phone: Basic Settings: Time Zone: GMT+1:00
Phone: Basic Settings: Daylight Savings Time: Yes
Phone: Basic Settings: Daylight Savings Time Rule: 3,-1,7,2,0;10,-1,7,2,0;60 (proved for Central Europe)
Phone: Advanced Settings: Admin Password: <telAdminPassWord>
Phone: Advanced Settings: Local RTP port: 5104
Phone: Advanced Settings: Keep-alive interval: 20 seconds
Phone: Advanced Settings: Use NAT IP: <empty>
Phone: Advanced Settings: STUN server: stun.sipgate.net:10000
Phone: Advanced Settings: NTP Server: 0.debian.pool.ntp.org
Phone: Account 1: Account Active: Yes
Phone: Account 1: SIP Server: sipgate.de
Phone: Account 1: Outbound Proxy: <empty>
Phone: Account 1: SIP User ID: <nonnumericSipgateIdent>
Phone: Account 1: Authenticate ID: <nonnumericSipgateIdent>
Phone: Account 1: Authenticate Password: <sipgatePassWord>
Phone: Account 1: Name: <givenNameSurName>
Phone: Account 1: Use DNS SRV: Yes
Phone: Account 1: SIP Registration: Yes
Phone: Account 1: Unregister On Reboot: Yes
Phone: Account 1: Register Expiration: 10 minutes
Phone: Account 1: Local SIP port: 5160
Phone: Account 1: SIP Registration Failure Retry Wait Time: 20 seconds
Phone: Account 1: NAT Traversal (STUN): Yes (detected NAT type is full cone)
Phone: Account 1: Voice Mail UserID: 50000
Phone: Account 1: Send DTMF: via RTP (RFC2833)
Phone: Account 1: SRTP Mode: Disable
Phone: Account 2: Account Active: Yes
Phone: Account 2: SIP Server: bluesip.net
Phone: Account 2: Outbound Proxy: <empty>
Phone: Account 2: SIP User ID: <nonnumericBluesipIdent>
Phone: Account 2: Authenticate ID: bluesip/<nonnumericBluesipIdent>
Phone: Account 2: Authenticate Password: <bluesipPassWord>
Phone: Account 2: Name: <givenNameSurName>
Phone: Account 2: Use DNS SRV: Yes
Phone: Account 2: SIP Registration: Yes
Phone: Account 2: Unregister On Reboot: Yes
Phone: Account 2: Register Expiration: 60 minutes
Phone: Account 2: Local SIP port: 5062
Phone: Account 2: SIP Registration Failure Retry Wait Time: 20 seconds
Phone: Account 2: NAT Traversal (STUN): Yes (detected NAT type is full cone)
Phone: Account 2: Voice Mail UserID: <empty>
Phone: Account 2: Send DTMF: via RTP (RFC2833)
Phone: Account 2: SRTP Mode: Disable
Phone: Account 3: Account Active: No (GXP2010 never worked well with more than 2 active accounts)
Phone: Account 4: Account Active: No (GXP2010 never worked well with more than 2 active accounts)
More on configuration:
1. Telnet should be used to configure both the router and the bridge to get rid of any trouble with keys.
Telnet should be disabled when finished.
2. The /jffs-filesystem on the router looks as follows, it should manually be installed accordingly.
drwxr-xr-x ... /jffs
drwxr-xr-x ... /jffs/etc
-rwxr-xr-x ... /jffs/etc/CreateCert
-rw-r----- ... /jffs/etc/SmallSystemsAccessData
-rw-r--r-- ... /jffs/etc/cacert.p12
-rw-r--r-- ... /jffs/etc/cacert.pem
-rw-r--r-- ... /jffs/etc/cert.p12
-rw-r--r-- ... /jffs/etc/cert.pem
-rw-r----- ... /jffs/etc/key.pem
-rw-r----- ... /jffs/etc/privkey.pem
drwxr-xr-x ... /jffs/tmp
drwxr-xr-x ... /jffs/tmp/ipkg
drwxr-xr-x ... /jffs/usr
drwxr-xr-x ... /jffs/usr/bin
-rwxr-xr-x ... /jffs/usr/bin/DlinkDsl320bReboot
-rwxr-xr-x ... /jffs/usr/bin/EatonNmc66102Reboot
-rwxr-xr-x ... /jffs/usr/bin/FixCronBug
-rwxr-xr-x ... /jffs/usr/bin/GrandstreamGxp2010Reboot
-rwxr-xr-x ... /jffs/usr/bin/MountExternalMemory
-rwxr-xr-x ... /jffs/usr/bin/UpdateCert
-rwxr-xr-x ... /jffs/usr/bin/UpdateLdSoCache
-rwxr-xr-x ... /jffs/usr/bin/wget
The files /jffs/etc/cacert.p12, /jffs/etc/cacert.pem, /jffs/etc/cert.p12,
/jffs/etc/cert.pem, /jffs/etc/key.pem, and /jffs/etc/privkey.pem
have to be created executing /jffs/etc/CreateCert on the router, once.
The file /jffs/etc/privkey.pem is basically useless but it is maintained here for consistency.
After signing the server certificate, cert.pem, the private key belonging
to the self signed issuer root CA, cacert.pem, is given up such that the issuer
root CA can no longer sign anything. Hence, the issuer root CA is trustable.
The PKCS#12 certificate files cacert.p12 and cert.p12 have to be imported by those
browsers that want to access the router via https://<myHostName>.<mySecondLevelDomain>.<myTopLevelDomain>:8443.
The password to import both cacert.p12 and cert.p12 is qwert123.
Once imported into the browser data base, the properties of the root CA, cacert.p12, must
sometimes be edited in the sense that one has to define what that certificate should certify.
Further, on those machines that want to access the router via ssh and friends, the files
cacert.pem and cert.pem can be installed as issuer_at_<myHostName>_<mySecondLevelDomain>_<myTopLevelDomain>.pem and
<myHostName>_<mySecondLevelDomain>_<myTopLevelDomain>_8443.pem, under /etc/ssl/certs, or, wherever the certificates
reside. Do not forget to execute commands in accordance with
c_rehash /etc/ssl/certs
and/or
c_rehash /etc/ssl/certs | grep WARNING
after installing files under /etc/ssl/certs.
The file /jffs/etc/SmallSystemsAccessData has to be edited and installed on the router.
The file /jffs/usr/bin/UpdateLdSoCache has to be installed on the router as-is.
For /jffs/usr/bin/wget click onto the link.
3. Executing /jffs/usr/bin/FixCronBug on build 18007 for GW2358-4 is of vital importance,
the cron scripts are ignored otherwise.
4. Furthermore, the script SetSshdAuthorizedKeys has to be edited and copied into /tmp on
the router before it has to be executed there one time. SetSshdAuthorizedKeys provides
public keys of particular SSH clients to the router such that those clients can access
the device without a password. So, some backup script running on a far away notebook
can do its job in the background without any user intervention, for example.
5. Regardless whether a CF card or an USB stick is used as the external memory,
the identifier of the first partition should be changed to 83, Linux,
and the partition itself should be formatted creating an ext2 filesystem.
Both fdisk and mkfs.ext2 are available on build 18007.
6. The following section should be placed into the system-wide OpenSSH SSH client configuration file,
/etc/ssh/ssh_config, before the Host * section.
Host <myHostName>.<mySecondLevelDomain>.<myTopLevelDomain>
StrictHostKeyChecking no
UserKnownHostsFile /dev/null
Once more, this section is placed into the file /etc/ssh/ssh_config on those machines that
will access the router via slogin root@<myHostName>.<mySecondLevelDomain>.<myTopLevelDomain>.
Such an entry causes that the file ~/.ssh/known_hosts on the client will be left alone.
Timetable:
At 0312 hours: Bridge reboots itself via Administration Keep Alive entry (if it is not stored in some drawer)
At 0317 hours: ADSL modem is rebooted by the router via cron script DlinkDsl320bReboot (that does not change the WAN IP address)
At 0322 hours: Router reboots itself via Administration Keep Alive entry (that does change the WAN IP address)
At 0327 hours: Phone is rebooted by the router via cron script GrandstreamGxp2010Reboot
At 0332 hours: UPS NMC is conditionally rebooted by the router via cron script EatonNmc66102Reboot
More scripts:
For more scripts see also DdwrtControl and ResetAllMySmallSystems.
Observations:
1. Not considering PowerLAN, the system behaves as expected at all times,
exhibiting outstanding reliability and performance.
Many thanks for the great work of all the parties concerned.
2. With respect to the audio quality, the Grandstream GXP2010 is very good.
3. Sipgate seems to be a reliable provider.
Sipgate uses unusual port numbers in some cases.
Some trouble described under point 8. of Observations in Experimental VoIP Setup
disappeared. Sipgate is now able to resolve a Bluesip ENUM entry of the form +4989...
without any problem, as others also are for a long time.
4. Bluesip is a very reliable provider.
5. The present setup, designed for a single-family house in a serene environment,
is the result of certain experiences with the Experimental VoIP Setup for some
metropolitan area. The most important experience is that the CPU power of a single
Linksys WRT54GL v1.1 system is too small to act as both a convenient router and a
WLAN access point when real-time applications as VoIP phones play a role. The
workaround there was to use two Linksys WRT54GL v1.1 systems to distribute the load,
one system acted as the router with the VoIP phone connected and the other as the
WLAN access point. Therefore, carrier class hardware was envisaged for the present
setup instead of two systems, to simplify the logic and to have some reserve behind.
And the expectation was appropriately high. So, finding out that the initial Gateworks
GW2358-4 router board, see photograph 2, came with a temperature problem this way
was quite the disappointment, especially because a heatsink had meanwhile been mounted
on the main circuit by means of thermally conductive adhesive.
The temperature problem can be described as follows.
Above about 38°C CPU temperature, seen with Status->Router->CPU->"CPU Temperature", the
WAN interface ixp1 got slowly lost. If the environmental temperature decreased,
such that the CPU temperature followed downwards from a value not essentially higher
than 38°C to, let us say, 35°C, then the WAN interface came back by itself.
If, on the other hand, the CPU temperature once went up to 47°C, being a completely
normal working temperature without active cooling, the WAN interface
could only be reenabled by means of the reset button. So, in winter all worked fine,
and, in summer with environmental temperatures of 35°C and higher, as actually observed,
the router enduringly failed to work, even with a heatsink and two 5 W fans
permanently switched on. Such a behavior is clearly out of the board specification.
Fortunately, NewMedia-NET GmbH (www.dd-wrt.com) unbureaucratically replaced the GW2358-4.
As seen on photograph 3, the new GW2358-4 board still runs without a heatsink, at
CPU temperatures that are of course higher than the ones that would be achieved with
the Fischer 5.2 K/W heatsink, but all works fine now.
Finally, on a Gateworks Cambria GW2358-4 network platform driving an Ubiquiti XR2, there
is enough CPU power to run all the services of the present plus some more of the future.
6. The bandwidth management of the Ubiquiti XR2 WLAN card is impressive.
7. Because of the trouble with the router board described under 5., there was plenty room
to study the behavior of the media converters EL022V2 with respect to their
Link Fault Pass-through (LFP) functionality.
These media converters carry IPv4, PPPoE and other packages, no issues were observed.
8. The GW2358-4 supports CompactFlash and USB mass storage devices.
If there is only one mass storage device installed than that device can be accessed
via /dev/sda, and if there exists only one partition then that partition is /dev/sda1.
Hence, the configuration remains the same, whatever type of device is installed so far.
A SanDisk Extreme III 2 GB CF card was firstly given a try. All went well up to
the moment a 600 MB file was copied from a remote host onto the CF card via scp,
then the file was read again via scp, and, finally, the copy was compared against
the original. The result was that original and copy differed from each other.
Performing the same with a file of about 20 MB, the copy equaled the original.
Such a behavior is not unknown to the author. It was seen on several hosts with different
devices, but all hosts ran Linux and all devices were IDE, as the CF cards, too. Next,
a Transcend TS32GJF600 32 GB USB flash drive was tested. All went well, with both
a 600 MB file and a 20 MB file, multiple times. Obviously, USB is better
supported at all. The plan to work with the faster CF cards was immediately given up.
9. Firmware bug.
While the firmware DD-WRT v24-sp2 (08/07/10) mini - build 14896
on the Linksys WRT54GL v1.1 systems does not exhibit visible bugs,
the firmware DD-WRT v24-sp2 (12/14/11) std - build 18007
on the Gateworks Cambria GW2358-4 network platforms does that.
Cron does not work as expected, as already reported above.
Just to know, the useless cron source /tmp/cron.d/cron_jobs does not contain ^M separators.
10. Bug in DD-WRT v24-sp2 (12/14/11) std - build 18007.
One has to observe the page with
Status->Bandwidth->"Bandwidth Monitoring - LAN",
Status->Bandwidth->"Bandwidth Monitoring - WAN" and
Status->Bandwidth->"Bandwidth Monitoring - Wireless (ath0)",
they do not reflect the reality in the following case.
There is a PC with WLAN and the user starts to watch a 1080p movie from the Internet.
WAN In correctly shows 14 Mbps average,
WLAN Out correctly shows 14 Mbps average,
LAN Out incorrectly shows 14 Mbps average.
11. Bug in DD-WRT v24-sp2 (12/14/11) std - build 18007.
Status->Router->"Space Usage"->JFFS2 shows 804.00 KB / 15.00 MB while
Administration->Management->"JFFS2 Support"->"Total / Free Size" shows 15.00 MB / -.
The latter must be a software bug.
12. The traffic shaping seems to work fine at all.
Up to the present, there is no practice oriented traffic
scenario that audibly interferes the telephone or the radio.
13. The trouble described under point 7. of Observations in Experimental VoIP Setup
led to the decision of substituting the traditional STUN based solution for Milkfish some day.
May be that recent Milkfishes are really better than ancient ones, but it was not tried again.
For one telephone, the STUN solution as set up here is robust and does not exhibit any issue.
14. PowerLAN. In countries where electrical installations are based on stranded copper wire and
a single phase only, PowerLAN is Plug and Play.
It works best with streaming applications, i.e., the achieved bandwidth is comparable to
the one of 100BASE-T, and the ping time can be compared with the one of WLAN IEEE 802.11g.
For short, if one is going to run NFS, a cable based installation is the only way.
With manually assigned passwords, PowerLAN seems to be secure and it is possible to have some
functionality similar to the one of VLANs, via different passwords. PowerLAN adapters with
different passwords assigned can coexist. Photograph 5 above shows how the guests of a garden
party can be made happy with their smart devices. There is no problem with a 100 m long extension
cord. PowerLAN has an intrinsic problem with power failures.
In countries with three phase electrical installations based on solid copper wire
the things do not go so smooth. PowerLAN on a three phase electrical installation
with a mixture of solid copper and solid aluminum wires is a challenge.
First tries surprised in the sense that nobody knows why a particular socket serves
for PowerLAN or even not, whereat the line routing is completely clear. It needs
further studies to find out what is going on with PowerLAN in such an environment.
15. The script to store some backup onto the router here has been qualified to
be compatible with the SSH access limitation to impede WAN DoS/Bruteforce attacks.
So, the SSH access limitation has been reenabled.
16. Since the end of May 2014, the Grandstream GXP2010 has not been registering anymore
when using the Bluesip STUN server. The GXP2010 has been saying that UDP is blocked.
The Sipgate STUN server has been substituted for the Bluesip one in the GXP2010
configuration to work around that problem so far.
TODO:
1. Currently nothing.
Sat, 10 Sep 2016 01:49:26 +0200
Stephan K.H. Seidl